Embarking on some IT documentation? Not sure what IT documentation you need to record? Perhaps we can help.
Computer networks are some of the most complex systems deployed within your organization. That complexity, coupled with notoriously poor documentation can lead to unacceptable levels of downtime, poorly performing applications, easily compromised security and unplanned expenses. Our Assurance Managed IT Services Onboarding Process seeks to quickly identify gaps in the documentation, performance, and supportability of systems. The process is quite intensive, taking a minimum of 3 days for our smallest clients and up to 2 weeks or more for larger environments. This is one of the reasons most managed IT services firms do such a poor job of it.
Based on our experience, here is a list of items you should have in your IT documentation.
A: SITE DETAILS:
- Address & Access Control
- Parking/Transportation info
- Site Liaison(s)
- Supplemental Cooling
- Power & Environmental
- Wiring/Data Closet Photos
- Floorplan / Office Layout
- End-User Contact Details
- Building Management Contacts
- Identification of temp/water sensors
- Age of backup batteries
- Equipment space constraints
- Building Entrance/DMARC identification
- UPS Protection Alerting
B: APPLICATIONS:
- Revenue generating apps
- Line of business apps
- Secondary apps
- Hosted applications
- IaaS, PaaS, SaaS, etc.
- Privileged Credentials
- Email/Collab Audit
- Network/App Dependencies
- Licensing
- Per-app RPO/RTO
- Application Logging
- Version Assessment
- Unlicensed apps
- Vital App Health Alerting
- Support Agreements
- Deprecated Software
- Malware Protection
- Print Management
- Network Detective Scan
- Scanning/Imaging
- Anti-Spam/Phishing
C: NETWORKING:
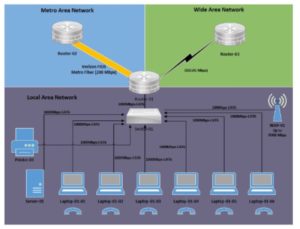
- Wiring Diagram(s)
- Block Diagram(s)
- Rack Diagram(s)
- Internet/WAN Providers
- Routing/Firewall Equipment
- Load Balancer Details
- Site Connectivity / VPN
- Equipment Aging
- Remote Access
- Cabling Assessment
- VoIP and Port Provisioning
- Content Filtering
- Station-Side Outlet Config
- Cloud Managed Devices
- Support Agreement Check
- Static IP Allocations
- Expired Firewall Rule Check
- Wireless Controller(s)
- Basic Site Survey / CCI Check
- SNMP Deployment
- SNTP Configuration
- DNS/DHCP Assessment
- IP Subnet Allocation
- Use of NAC/802.1x
- Circuit ID’s
- Device Login Security
- Spares/Recovery Options
- QOS/Traffic Shaping
- DNS Protection Measures
- Physical Security
- Network Appliances
- Cloud Integration (vNET/S2S/C2S/vFW)
- Device Inventory Report
- Critical Port Identification
- Redundancy Options
- Service Dependencies
- Syslog Deployment
- Configuration Backups
- Network Map / Discovery Validation
- Core/Edge Overview
- Version Assessment
- VLAN Architecture
- GeoIP Filtering
- Protected Supply Power
- Multi-Party Management
- DOS Attack Prevention
- Video/Security Integration
- ISP Speed Check
- Registrar/DNS Details
D: SERVERS & STORAGE:
- AD Architecture / Minimum Protections (2 AD hosts)
- Group Policy Collection
- Hypervisor Assessment
- Backup Assessment
- Recovery Test / RTO Validation
- Login Script Review
- Unrestricted User/PC Check
- SMTP Checks
- Time Synchronization Check
- DFS Health Inspection
- Site Object Validation (Sites/Subnets/GC’s)
- General Drive Mappings
- Server Print Management
- Terminal Services Review
- Farm / Cluster Node Review
- Equipment Aging
- HCL Validation
- FSMO Roles / AD Schema
- Cloud Sync Tools (AAD)
- Licensing Check
- Storage/iSCSI/RAID Check
- RAID Management & Alerting
- Deprecated OS Check
- Malware Deployment and Exclusion Check
- Domain Security Policy
- Driver/Patch Validation
- Log Review
- Firmware Check
E: DESKTOPS:
- Key Personnel Review
- Agent Deployment
- Log Review
- Malware Inspection
- Patch / Driver Review
- Equipment Aging
- Desktop Imaging Tasks
- Local Applications
- Domain/Workgroup Assessment
- Deprecated OS Check
- Print Management
- Local Security
- Local Plug-In’s
- Folder Redirection / Profile Management
- License Validation (Windows, Office, etc.)
- Security / Open Port Scan
- Failed Login Attempts
- Remote Control Policy
F: OTHER:
- Single Source of Identity
- Strong Security (2FA)
- Self Service Password Change Availability
- Single-Sign-On (Azure, Okta, etc.)
- Security Awareness Training
- SRA Discussion
- Mobile Device Policies
- Email Protection (SPF, DKIM, DMARC)
- Governance & Compliance
- Device Isolation for Wireless or PCI-DSS
- IoT Readiness (if applicable)
- POS terminals (if applicable)
- Disaster Recovery
- Outdated Mobile Device Cleanup
- Partner Cloud Authorization
- Warehouse automation (if applicable – scanners, timeclocks, etc.)
An IT documentation project is no trivial task. Need help? Contact us. Need large, complex Wi-Fi network design in Colorado? Check out our sister company, SimpleFly!
Daniel Haurey Jr. is the president and founder of managed IT services provider Exigent Technologies, which he founded in 1997. Under his leadership, the MSP has earned accolades ranging from Channel Futures MSP 501 to being named SonicWall’s 2024 MSP Growth Partner of the Year. Dan is a true entrepreneur, dedicated to growing, investing in, and mentoring small businesses. You can find him on LinkedIn, where he regularly posts about technology, business, leadership, and community.
