If you are among the 66% of business leaders who are more concerned about cyber attacks this year than last, then the obvious next question is: what are you doing to protect your business?
Sure, there are incredibly effective cybersecurity solutions that your managed services provider (MSP) can deploy to combat all types of network security threats, but there are common network vulnerabilities that can be addressed quickly—often while a deeper assessment of your cybersecurity stance is handled by your technology partner.
Within any tech environment, there are many, many types of vulnerabilities in network security, but these are common network vulnerabilities that businesses often overlook and that can provide an unguarded opening for cybercriminals.
We recently dedicated an entire blog to multifactor authentication (MFA) and the key role it plays in cybersecurity.
While the debate for years has revolved around replacing weak passwords with strong passwords to create higher barriers against unauthorized access to business systems, MFA is one of the most effective options for securing networks from cyber attacks.
If your employees can log in to their business email or your network without being challenged from a secondary device, such as a smartphone, then you are likely vulnerable to attack.
Hackers constantly test security and access points, and one of the best ways to penetrate a network is through one of your team member’s passwords.
Remember, access to email opens the door to your entire business network, so start considering MFA as a necessary layer of protection, not an extra layer.

Technology can be expensive, so it’s likely there are pockets of outdated software or chunks of obsolete hardware in your network. Those unsupported pieces of technology provide a prime window of opportunity for hackers to gain access to sensitive data in your business network.
Nearly every type of technology reaches a point where vendors either end support or simply can no longer maintain support for the dated solution.
Nearly everyone has seen end-of-life notifications for operating systems on mobile devices—alerts from a vendor such as Apple or Lenovo that advises you that continuing to use the OS or device will put your data at high risk.
That means no more security patches and no more updates to close security vulnerabilities. If you are pursuing cyber insurance, one key question you will be asked requires identifying all obsolete technology in your network because of the security risk posed by those products and devices.
Safeguard Your Business with Cyber Security Protection at Expert LevelLet Exigent Help You Navigate the Current Threat Landscapes |
Patching is one of the low-cost, high-impact cybersecurity practices any organization can tackle. When evaluating a managed IT services provider, a clear schedule and well-defined policy around regular and aggressive patching should be high on your checklist of “must-haves.”
Why is patching so essential? According to a Ponemon Institute report, 57% of cyberattack victims say the breach could have been prevented by installing an available patch, and 34% said they knew about the vulnerability, but hadn’t acted to stop it.
Additionally, 78% of organizations report they don’t patch critical vulnerabilities within 24 hours of availability, leaving the entire network vulnerable.
With application vulnerabilities among the most common paths for a cyber attack, frequent application patching is what separates victims from targets.
Now would be the time to either review your patch management policy and standard process for addressing unpatched software or raise the issue with your MSP to fully understand what their advice is for eliminating that vulnerability.
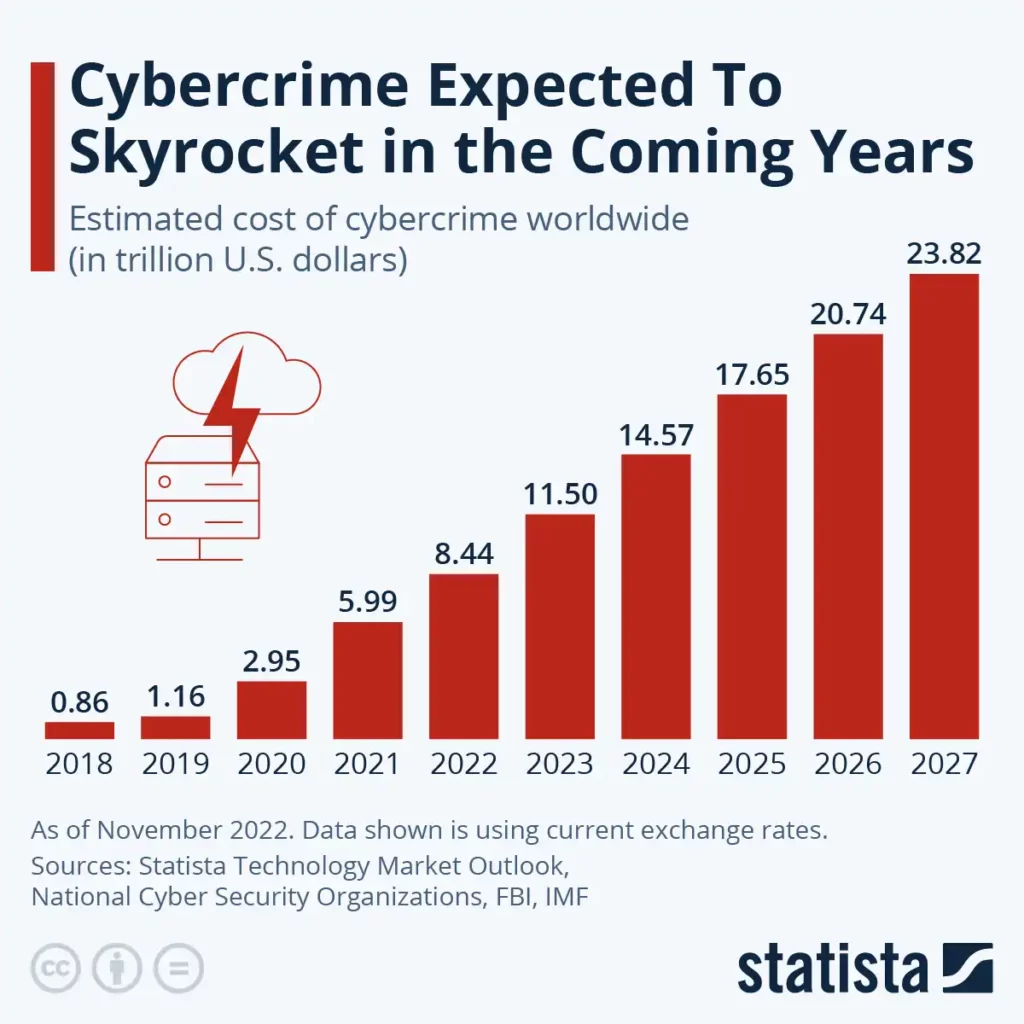
In a 2022 threat detection report, cybersecurity vendor Arctic Wolf highlighted data revealing that more than 47% of threats included a compromised cloud component.
Their report also disclosed that 92% of organizations have an active cloud security gap within
their infrastructure.
Moreover, fewer than 40% of the respondents to an Arctic Wolf survey believed they are effectively securing their cloud resources.
That raises the question of how you are evaluating your cloud solutions for network security vulnerabilities.
Is security a key element in your cloud computing strategy? Check out these additional resources to learn more about how a cyber security checklist can come in useful.
Resources: |
Cloud security vulnerability assessments, including penetration testing and ethical hacking tests, can be well worth the network security investment compared to the multimillion-dollar cost of a data breach.
Cloud solutions can be particularly vulnerable due to misconfigured security settings, heavy reliance on APIs, and a lack of visibility into the security stance of cloud service providers.
A common and simple distributed denial of service (DDoS) attack can wreak havoc on cloud solution users. Cybersecurity assessments, cloud-specific security solutions, and ongoing cybersecurity reviews of your cloud products are key to reducing this vulnerability.
Most cyber attacks—91%—start with a phishing email.
That makes employees your first and best line of defense, as well as your biggest network vulnerability.
The good news is that your team is the security gap most easily addressed. Implementing a cybersecurity awareness program and training ranks as the second-highest choice of cybersecurity investment for businesses in 2023.
When your team understands what a social engineered or phishing threat looks like, and how to respond, your organization takes a monumental step forward in the battle against network security vulnerabilities.
Proactively and regularly reminding your employees about the telltale signs of a risky website, phishing email or other malicious tricks that open the door to a cyber attack can be one of the easiest ways to improve your security stance.
You are well on your way to a protected environment when training is paired with active monitoring technology.

While all five of these common network vulnerabilities are fairly easy to address, most businesses will need professional support to truly eliminate these and other common security vulnerabilities.
Partnering with an experienced managed services provider (MSP) can be one way to reduce your vulnerabilities.
That being said, it’s necessary that you evaluate your chosen IT provider’s understanding of cyber threats and vulnerabilities – and closely review their policies for systematically assessing cyber vulnerabilities to help you maintain good cyber security posture.
Remember, just as the types of attacks aimed at your network continue to evolve and become more and more sophisticated, so must your cybersecurity roadmap and approach to protecting your environment.
Find out how Exigent Technologies can help you stay protected with cybersecurity consulting! Book your free consultation today.
Daniel Haurey Jr. is the president and founder of managed IT services provider Exigent Technologies, which he founded in 1997. Under his leadership, the MSP has earned accolades ranging from Channel Futures MSP 501 to being named SonicWall’s 2024 MSP Growth Partner of the Year. Dan is a true entrepreneur, dedicated to growing, investing in, and mentoring small businesses. You can find him on LinkedIn, where he regularly posts about technology, business, leadership, and community.