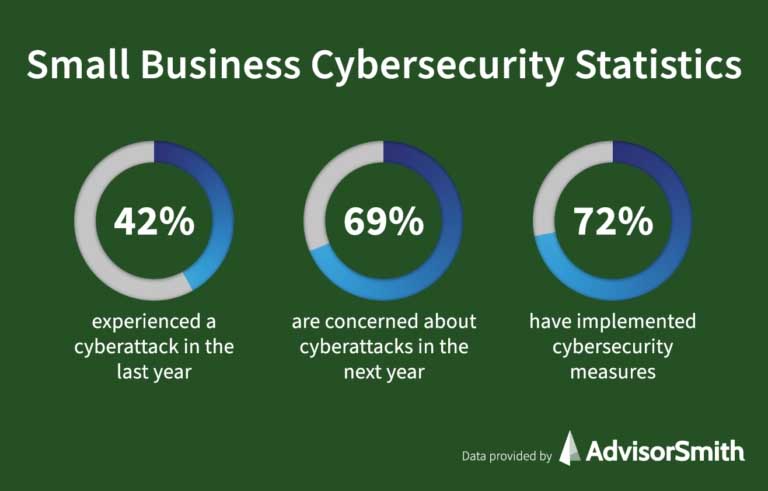
According to recent cybersecurity research, 69% of businesses are concerned about their cybersecurity and risk management solutions. In exploring the following cyber attack statistics, it’s easy to understand why.
While cyber insurance is custom-built for today’s digital business footprints, it can be overwhelming to try to understand, evaluate, and prepare to apply for cyber insurance coverage on your own.
To simplify the process, let’s review the elements of a cyber insurance policy and the steps your business needs to take to secure insurance coverage, including completing a cyber insurance coverage checklist.
There are three common segments within every cyber insurance policy: First-party coverage, third-party liability and crime insurance.
For some companies, higher levels of certain types of coverage may be needed, particularly if your business secures personally identifiable data for clients or operates a vertical with particularly high cyber risks.
But overall, cyber insurance is similar to automobile insurance in that it covers both damage to your car as well as damage you may cause to another vehicle or property.
First-party coverage addresses the cost to businesses that are directly impacted by a cybersecurity incident. Typically, coverage includes the cost to manage data loss and interruption of business operations, extortion fees from ransomware, the financial impact of digital theft or hacking, and both deliberate and unintentional denial of service.
On the other side of the policy, cyber liability Insurance coverage applies to the third-party liability and certain penalties, fees and other costs stemming from damage to other companies or individuals.
Lastly, crime coverage can be included to specifically address concerns about invoice manipulation, social engineering fraud, computer fraud, and theft of computer services. Insurance providers expect all these criminal activities will continue to grow significantly.

Much like any insurance policy, the goal of cyber insurance coverage is primarily reimbursement of the financial losses caused by a cyber attack.
For example, first-party coverage may cover:
First-party coverage typically also covers credit monitoring and the crisis communications required as part of a data breach response plan. Third-party coverage, however, is entirely about liability, focusing on legal costs, PCI fines and penalties, as well as costs from regulatory inquiries.
Depending on the type of business you have, it pays to invest the time and effort into educating yourself about reputable insurance providers and exploring in detail the parameters of the coverage your business is considering.
Gain The Cyber Coverage You NeedDecision-Making Made Simple With Our Expert Insight |
While you research and evaluate cyber insurance providers, you should also evaluate and prepare your environment for review before applying for cyber insurance to improve your chances of securing coverage and better rates.
The place to start is with a cyber insurance coverage checklist.
A checklist is a scorecard document that consolidates the facts about your technology environment and security standing for easier review.
Most insurance companies will require a cyber insurance coverage checklist to be completed before considering your business for coverage, so tackling this element of the process early on can accelerate your policy deployment.
Take Charge of Your Insurance Coverage!Download our Cyber Insurance Sample Prep Checklist |
In addition to using the checklist as part of your policy research, it can help to establish a baseline for where your company sits in the cybersecurity hierarchy and guide future decisions and technology investments.
Common topics and areas of concern for network security questions include:
Check out these additional resources to learn more about common cybersecurity best practices and why managed and professional services are your answer!
Resources: |
Many businesses, particularly small to medium-sized companies, may be shocked by what insurance partners are asking them to do to reduce exposure to cyber and technology risks, especially those companies relying on legacy computer systems.
For instance, legacy hardware and software may be seen as more vulnerable to a cyber incident and, therefore, riskier to cover.
The cyber insurance coverage checklist answers a simple question for companies: “How insurable am I?”
When an insurance provider evaluates a technology and policy environment for security risk, many businesses may find they are not able to meet the bar set for coverage.
Because cybersecurity is complex, with quickly evolving threats and attacks that can shift focus in a flash, having an outsourced cybersecurity and managed services partner may be the best solution for your SMB.
With a full team of experienced cybersecurity and compliance experts, Exigent Technologies can begin by assessing your cybersecurity stance and attack vectors.
By using a full arsenal of methods, such as ethical hacking and penetration testing, alongside a full assessment of your current technology and cybersecurity solutions, we help create a sensible, affordable roadmap that ensures your business will meet the high standards demanded by cyber insurance providers.
Book a free consultation to learn more about how we can help.
Daniel Haurey Jr. is the president and founder of managed IT services provider Exigent Technologies, which he founded in 1997. Under his leadership, the MSP has earned accolades ranging from Channel Futures MSP 501 to being named SonicWall’s 2024 MSP Growth Partner of the Year. Dan is a true entrepreneur, dedicated to growing, investing in, and mentoring small businesses. You can find him on LinkedIn, where he regularly posts about technology, business, leadership, and community.